Gaurav Dhy and Elijah Snyder
Securing data in complex cloud-native environments is challenging, but it doesn’t have to be. This blog series delves into the best practices for leveraging HashiCorp Vault within Kubernetes environments. The coming blog posts cover comprehensive guidelines on deploying Vault, managing secrets, implementing robust access controls, and ensuring audit and compliance tracking. By leveraging these insights, organizations can enhance their security posture, streamline operations, and ensure compliance with industry regulations.
This series offers the detailed guidance needed to secure Kubernetes deployments effectively, whether you’re looking to set up Vault for high availability, manage dynamic secrets, or establish detailed access policies.
Vault Deployment in a Kubernetes Environment Best Practices
- Vault Installation and Configuration: Guidelines for deploying Vault in a Kubernetes cluster, including considerations for High-Availability (HA) setups.
- Secrets Management: Best practices for managing and accessing secrets in Kubernetes with Vault.
- Access Controls: Implementing policies and roles that dictate who can access what secrets, and under which conditions.
- Audit and Compliance Tracking: Ensuring that all access and usage of secrets are logged for compliance and security monitoring.
Vault Installation and Configuration
Deploying HashiCorp Vault within a Kubernetes environment requires planning and configuration to ensure it operates securely and efficiently. This section provides an outline of setting up Vault with a special focus on considerations for high-availability configurations.
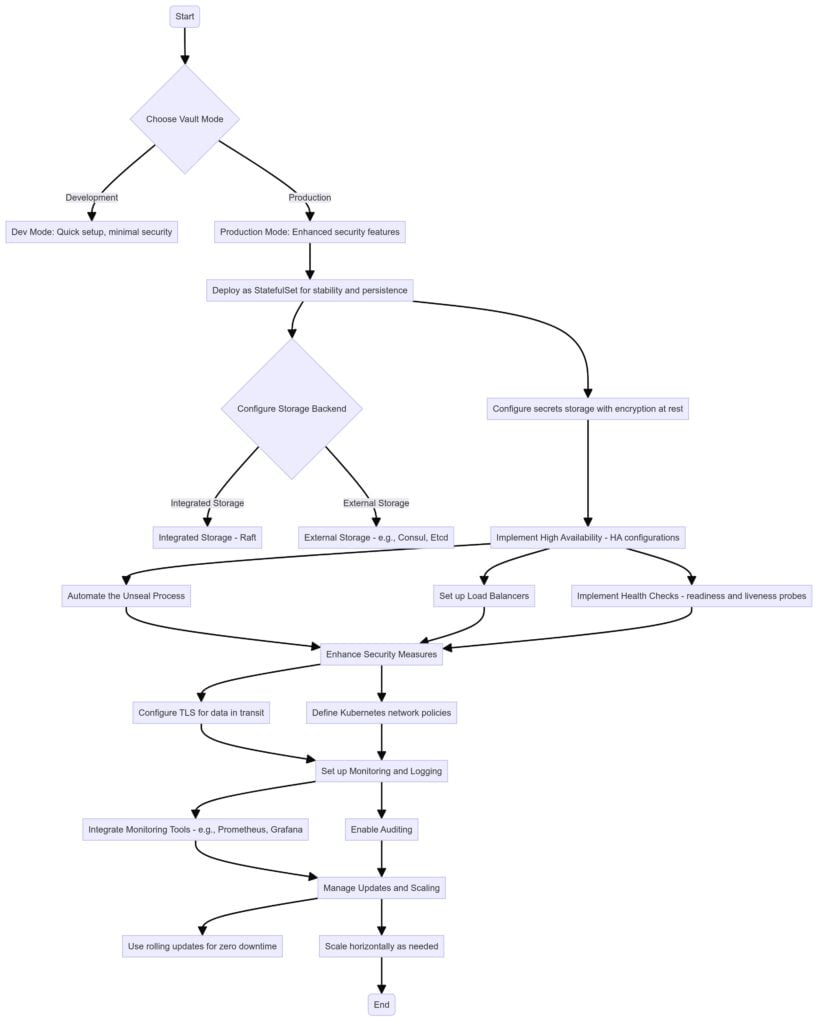
- Choosing the Right Vault Mode
- Dev Mode: Suitable for evaluation, development, and testing, Dev Mode offers a simplified setup where Vault operates with minimal security features. It is not suitable for production but can give your developers a head start on adopting a secrets management solution.
- Production Mode: For production environments, Vault should be deployed in production mode. Production mode supports enhanced security features like TLS encryption, detailed logging, and more.
- Vault Deployment Strategies
- StatefulSet Deployment: Kubernetes StatefulSets are ideal for deploying Vault because they provide stable and unique network identifiers and persistent storage necessary for Vault’s operation.
- Deployment Configuration: Include a minimum of three Vault nodes to ensure fault tolerance. Configure each node to communicate over HTTPS. This configuration helps to maintain data confidentiality and integrity.
- Storage Backend Configuration
- Integrated Storage (Raft): For simpler setups and easier operations, use Vault’s integrated storage, which supports HA configurations by default and simplifies the operational overhead. Integrated Storage is supported by HashiCorp support.
- External Storage: For large-scale deployments, consider using external storage solutions like Consul or Etcd. Ensure they are configured for HA and network partition resilience. We usually recommend etcd over Consul. HashiCorp may provide only limited support for external storage.
- Handling Secrets Storage
- Encrypting Data at Rest: Use Vault’s ability to encrypt data at rest. Ensure that encryption keys are stored securely and access is tightly controlled.
- Dynamic Secrets: Utilize Vault’s dynamic secrets capabilities to manage temporary credentials that are automatically revoked when no longer needed.
- High Availability (HA) Considerations
- Load Balancing: Deploy a load balancer in front of Vault nodes to distribute requests evenly. This prevents any single node from becoming a bottleneck and ensures smoother performance and reliability.
- Unseal Process: The sealed state in the HashiCorp Vault is a security feature where the Vault is locked down and unable to access or decrypt any of its stored secrets. When the Vault starts in a sealed state, the unseal process involves using multiple keys to access and decrypt stored data. Automate the unseal process using Kubernetes secrets or integrate with a cloud provider’s key management service to enhance security and streamline operations.
- Health Checks: Implement readiness and liveness probes in your Kubernetes configuration to monitor the health of Vault nodes and automatically handle failures.
- Security Enhancements
- Network Policies: Define Kubernetes network policies to restrict who can communicate with the Vault pods, limiting access to trusted applications.
- TLS Configuration: Always use TLS to encrypt data in transit. Manage and rotate TLS certificates with an automated process to maintain strong security.
- Monitoring and Logging
- Enable Auditing: Turn on auditing in Vault to keep a detailed log of all operations. Store audit logs securely and analyze them regularly for security insights and compliance.
- Integrate Monitoring Tools: Utilize tools like Prometheus and Grafana for monitoring Vault’s performance and operational metrics. Set up alerts to notify administrators of potential issues.
- Updating and Scaling Vault
- Rolling Updates: Use Kubernetes rolling updates for deploying updates to Vault without downtime.
- Scaling: Scale Vault nodes horizontally by increasing the number of replicas in the StatefulSet as demand grows. Ensure the load balancer and storage backend can handle the increased load.
By following these guidelines, you can ensure that your Vault installation is robust, secure, and well-suited to your Kubernetes environment. We recommend carefully testing each step in a staging/pre-production environment before rolling out to production.
Vault Installation and Configuration Considerations Visual
In our next post, we’ll dive into how HashiCorp Vault provides a robust solution for managing secrets in Kubernetes environments.

