Gaurav Dhy and Elijah Snyder
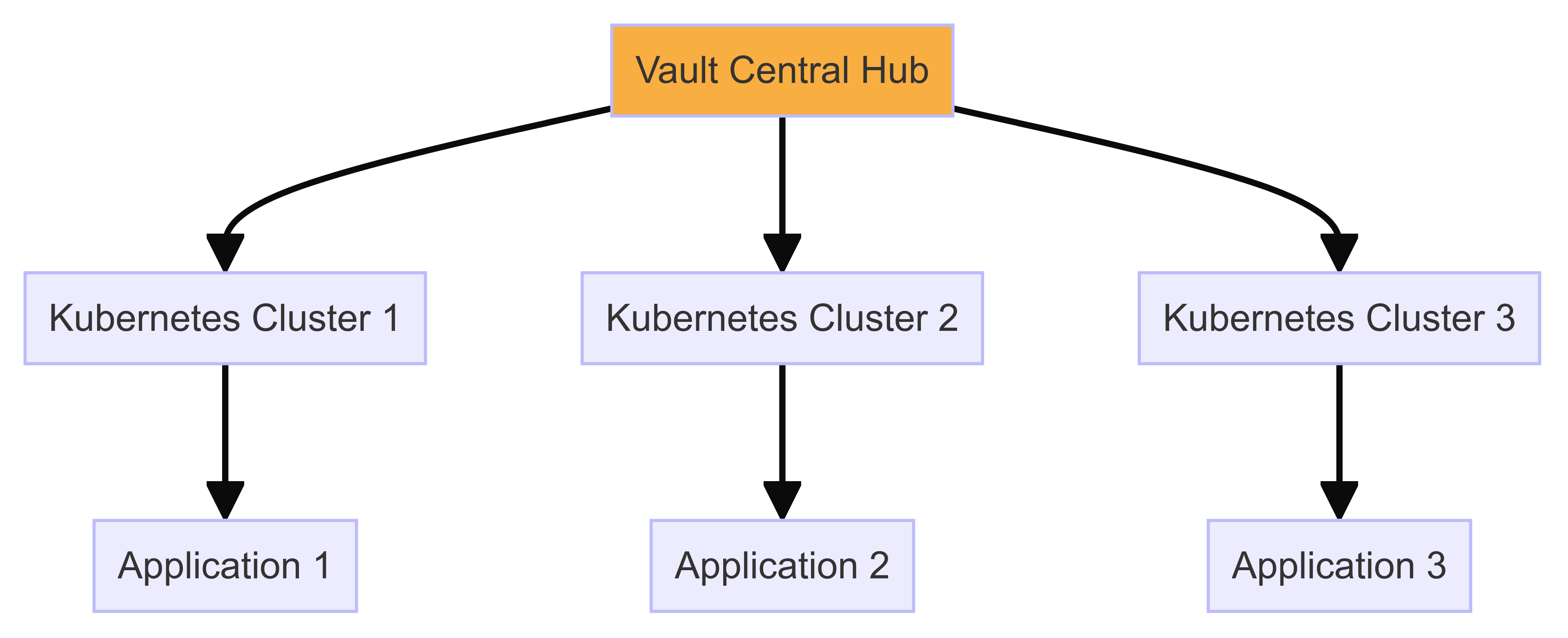
Kubernetes is an amazing tool, but handling sensitive information like passwords, tokens, and API keys within Kubernetes environments can be a bit of a headache. In that context, HashiCorp Vault can be a powerful tool for streamlining and securing secrets.
But first, why even bother with a centralized secrets management system? In our world, where applications and services are scattered across various environments, it’s crucial to keep all those secrets in one secure spot. This not only improves your security but also simplifies your entire secret management process. With Vault, you’re putting all your secrets in one basket. Don’t worry, it’s a really secure basket.
In this post, we’ll walk you through some secret management best practices with Vault. Let’s start.
1. Configure Your Secrets Storage
Secure Storage: Choosing the right encryption standard is crucial for securing your secrets. Below is a table to help you choose the most suitable encryption method based on your specific use cases.
Encryption Standard | Description | Typical Use Cases |
AES-256 | Symmetric encryption with a 256-bit key for high security. | General purpose for encrypting data at rest; widely accepted and secure. |
AES-256 GCM | AES in Galois/Counter Mode offering encryption and authentication. | Preferred for environments where both data confidentiality and integrity are critical. |
RSA | Asymmetric encryption, useful for secure data transmission. | Encrypting data in transit, especially for initial exchanges like sharing unseal keys. |
ChaCha20-Poly1305 | Stream cipher providing high performance and security. | Suitable for environments where software performance is critical, and hardware support for AES is limited. |
2. Dynamic Secrets
Use Dynamic Secrets: Leverage Vault’s dynamic secrets capabilities to generate secrets on-demand for systems interacting with your Kubernetes environment. Dynamic secrets are generated for a specific duration and are automatically revoked and deleted when they expire, reducing the risk associated with static, long-lived credentials.
Automate Credential Rotation: Configure Vault to automatically rotate secrets at predefined intervals. This practice minimizes the potential impact of secret leakage, as credentials are only valid for a short period.
Dynamic secrets can prevent secret sprawl and expose credentials. Even if team members add secrets to password managers, git or other VCS repos, or their personal notes, the short-lived nature of dynamic secrets will prevent exposure and misuse of these secrets, which may end up in non-secure locations.
3. Fine-Grained Access Control
Define Policies and Roles: Define comprehensive access policies in Vault that specify which users or services can access certain types of secrets. Utilize roles to manage permissions and enforce least privilege access, ensuring that entities have only the permissions necessary to perform their tasks.
Integrate Service Accounts: Integrate Kubernetes service accounts with Vault to streamline the authentication process. By binding Kubernetes service accounts to specific Vault policies, you can simplify credential management and ensure that Kubernetes pods have appropriate access to the necessary secrets.
4. Secrets Injection into Pods
Sidecar and Init Containers: Use Vault’s sidecar or init containers to inject secrets directly into Kubernetes pods. This method ensures that secrets are not exposed within the pod configuration or stored in less secure locations.
Environment Variables vs. Volume Mounts: Decide whether to inject secrets as environment variables or as files mounted on volumes based on your security requirements and application design. While environment variables are easier to use, volume mounts provide better security as they avoid exposing secrets in pod metadata.
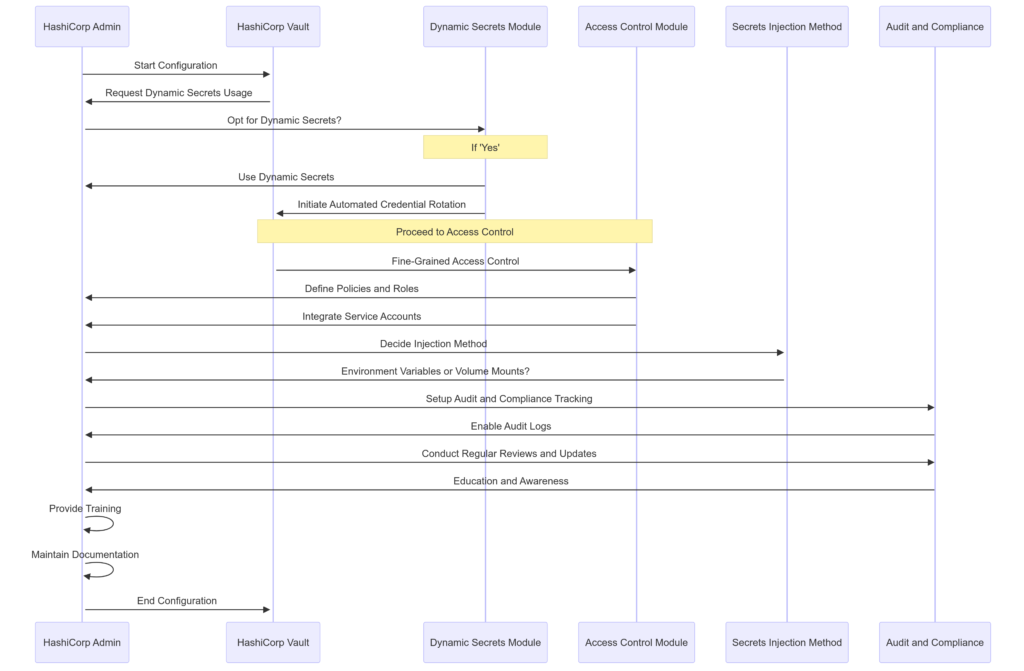
We hope this post has provided you with useful insights into managing secrets effectively in Kubernetes with HashiCorp Vault. By centralizing secrets storage, leveraging dynamic secrets, enforcing fine-grained access control, and securely injecting secrets into pods, you can significantly enhance the security and efficiency of your operations.
Stay tuned for our next post, where we’ll dive deeper into advanced access controls. We’ll explore how to implement robust access policies using Vault’s capabilities to ensure that the right people and applications have the right access at the right time, to ensure you have a watertight security posture in a Kubernetes environment.